This short terrorism futures essay will focus upon differing forms of targeting and their effects, that is, destructive versus disruptive, and the interrelationship between these and the scale of effect of weaponry in engagements, highlighting the differences between legitimate state use of coercion and the illegitimate use of disruptive targeting—and the subsequent magnification of the scale of effect of weaponry in engagements—when employed by terrorists. It will conclude with a discussion of the counter-threat implications of acknowledging terrorism as a form of disruptive targeting and the need for states to focus on new counter-threat protocols that go beyond physical consequence management and instead also include the protection of societal bonds.
Terrorism Versus State Coercion
States as legitimate sovereigns seek to utilize coercion via the certainty of punishment by means of fines, incarceration, and—in certain circumstances—capital punishment to enforce societal norms and rules to both protect and benefit its citizens and foreign nationals residing within its borders. The end result sought is one in which the integrity of society is maintained for the public good and the bonds and relations between the governed and the government remain positive and strong. Acknowledged tradeoffs between personal freedoms and security are an accepted component of the metrics related to a state’s use of internal coercion directed against its citizenry. Failure to maintain balance—derived from historical norms of expected governance—may result in civil protest and unrest, especially if perceptual gaps exists such as between a minority of the populace and larger components of society. This issue has recently come to the fore with race and justice issues in the United States related to the Ferguson incident [1].
A legitimate state’s concerns over internal stability can be strongly contrasted to the use of terrorism by a non-state group acting independently or as a proxy for a foreign state [2]. Since the intent of terrorism is to degrade the internal stability of a state in order to achieve concessions and/or change governance to further its own group’s (or sponsor’s) policies, it is used to de-bond societal cohesion rather than reinforce it. The certainty of the use of coercion is thus of no utility to the terrorist who comes from a position antithetical to that of the state. Thus, an ambiguity in approach (or at least the perception of one) is strived for because it generates more apprehension within targeted populations due to the uncertainty if or when an attack may come and magnifies the resulting disruptive effects.
Destructive Versus Disruptive Targeting
When sovereign states—which are hierarchically based—undertake conventional warfare with one another, the natural form of combat targeting is destructive in nature. It is directed at ‘things’ such as people (the citizenry), the government, and the military of opposing states. Destructive targeting is thus very thing based—be it measured in ground seized, people captured or killed, or materiel destroyed.
A second form of targeting—known as disruptive targeting—has more recently been identified over the last few decades. This form of targeting is organic to more networked organizational forms such as non-state groups. Since evolved networks are, by their nature, redundant in information flows and have a capacity to self-heal by working around damaged nodes [3], they utilize disruptive means for conflict (fighting) purposes. Instead of targeting ‘things’ (such as people or nodes), the target sets attacked are the ‘bonds and relationships’ that connect things together [4]. Trust between citizens, civilian feelings of security within a society, and goodwill between the people and their government are but a few examples of such target sets.
Conventional military operations related to such targeting draw upon principles of psychological warfare and getting inside an opposing force’s OODA (observe-orient-decide-act) loop. Concepts of blitzkrieg (maneuver warfare) in which the actions of an attacking army causes cascading command and control (C2) failure and eventual paralysis within an opposing armed force also succeed by getting into this loop. The disruptive nature of this form of military targeting, however, is not generally emphasized given that it is still directed toward a parallel conventional force. Terrorism, by creating a climate of terror within the targeted population and thereby breaking the bonds of security and trust within society, on the other hand, represents a clearer form of disruptive targeting—one which is criminal (illegal) in nature and condemned for breaking the rules and conduct of civilized warfare and internationally agreed upon norms and laws.
Point, Area, and Systemic Effects
The scale of effect of weaponry in military and military-like engagements takes place at ever increasing levels of battlespace influence (e.g. operational space for policing). At the most basic level, point targets—that is individuals—engage utilizing bladed weapons and small arms. The next level of effect encompasses an area, essentially a cluster of points, which may include shooting at a line of individual targets or throwing a grenade into a grouping of targets.
The final level of effect is systemic in nature with the result that large clusters of individuals (or nodes) are being influenced by the attack or engagement. Large scale physical systemic effects are difficult to create with conventional (explosive based weapons and munitions) and bring us into the realm of CBRN (chemical, biological, radiological, and nuclear) [5] and information/cyber based attacks (drawing upon computer viruses and radio frequency (RFW)/high-power microwave (HPM) type weaponry) [6].
The scale of the effect of different weaponry and engagement patterns, however, combine with the type of effect of differential forms of targeting resulting in dissimilar end states for coercion and terrorism. With regard to the scale and type of effect, Figure 1. is illustrative of the difference between a tactical action (point—or even area—focused based on destructive targeting) and a terrorist event (systemic focused based on disruptive targeting) [7].
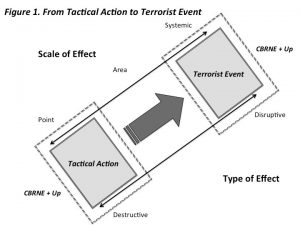
A terrorist attack, on its own, is basically meaningless when viewed from a conventional warfare perspective—it is typically equivalent to, at best, a squad sized force engagement. However, because such an attack is not about destructive potentials but rather focused on disruptive ones, it can readily result in systemic (strategic) level influence outcomes. One can think of the attack as dropping a pebble into a tranquil pond—the point of impact is inconsequential—rather the ripples created on the pond surface serves as the attacking mechanism [8].
Unlike when a conventional force engages in an action, a terrorist event results in a synergistic outcome. A tactical action by conventional forces targeting one individual or a group of individuals will result in physical damage to only the same number of those engaged. A terrorist event, however, may result in the death of a limited number of people but, because of its disruptive effects, ‘terrorizes’ at a systemic level all of those individuals who identify at some level with its victim(s). While the mechanism involved may be inherently irrational in nature, the attack plays on the fears of a state’s citizens and the disruptive effects of the attack are reinforced by the sensationalized and repetitive nature of 21st century global media.
Counter-Threat Implications
In line with the previous discussion, and as can be seen in Figure 2., the difference in the purpose of a state’s use of coercion (to—along with inducements—reinforce societal cohesion) versus that of non-state independent and state-proxy terrorism (to de-bond social cohesion) come into the equation. This terrorist offensive versus sovereign state defensive dynamic means that counter-terrorism response cannot be focused solely on threat force tactical actions and their destructive effects [9]. Too often, consequence management is ‘thing’ focused—the natural bias of states—with effort simply put into the treatment of those injured in an attack and the physical clean-up of incident scenes with lip service given to alleviate public fears. Given the Westphalian origins of modern states, protecting the integrity of the links between their government, people, and military sectors is paramount.
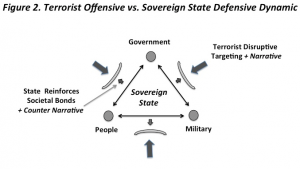
Hence, a state must also fully engage in non-physical consequence management—writ large—in response to a terrorist attack. This form of response is needed to both counter the ‘terrorist narrative’ (i.e. the policies and end states that they are promoting) that is a component of an attack and, potentially even more importantly, to make sure societal bonds and relationships (i.e. citizen’s trust in government, their feelings of security to engage in normal activities, and their sense of goodwill towards the military and law enforcement) have not been degraded or even potentially severed.
Given that advances in social media and global communications have moved us beyond 24/7 news channel platforms into torrents of live streaming information utilizing chats, tweets, and posts with embedded videos (some in real time), the disruptive potentials of terrorism will continually expand. It is imperative that sovereign states recognize such potentials by fully acknowledging the disruptive targeting basis from which terrorism is derived. In order to do so, they should now focus on implementing counter-threat protocols focusing on protecting and making resilient our vital societal bonds.
Notes
[1] Eliott C. McLaughlin, “What we know about Michael Brown’s shooting.” CNN. 15 August 2014, http://www.cnn.com/2014/08/11/us/missouri-ferguson-michael-brown-what-we-know/.
[2] Recent scholarship has attempted to shift traditional perceptions of terrorism from non-state groups (and, in some instances, their state sponsors) to now encompass specific internal policies and activities of states themselves. These perceptions fail to appreciate important categorical differences. For a work showing a possible exception with regard to a fully illegitimate regime, see Paul Rexton Kan, Bruce E. Bechtol Jr., and Robert M. Collins, Criminal Sovereignty: Understanding North Korea’s Illicit International Activities. Carlisle: Strategic Studies Institute, U.S. Army War College, 12 April 2010, http://www.strategicstudiesinstitute.army.mil/pubs/display.cfm?pubID=975.
[3] A basic primer on the differences between hierarchical and networked organizational forms is Ori Brafman and Rod A. Beckstrom, The Starfish and the Spider: The Unstoppable Power of Leaderless Organizations. New York: Portfolio, 2006.
[4] In addition to the author’s bond-relationship targeting (BRT) research, the older netwar writings of John Arquilla and David Ronfeldt associated with the U.S. Naval Post Graduate School and RAND, respectively, should be consulted. See, for example, their Advent of Netwar (RAND 1996) and Networks and Netwars (RAND 2001).
[5] This is typically designated as CBRNE with the E representing ‘explosives’ that fall under very broad U.S. Federal “weapons of mass destruction” criteria for prosecution and sentencing purposes. Explosives, however, do not organically have a systemic level scale of effect—still, the E is considered part of the ‘+ Up’ for destructive and disruptive effects.
[6] For some early thinking on these systemic effects, see Robert J. Bunker, “Weapons of Mass Disruption and Terrorism.” Terrorism and Political Violence. Vol. 12. No. 1. Spring 2000: 37-46.
[7] This figure is modified from Figure 7: BCB Scale of Effect and Type of Effect found in Robert J. Bunker and Christopher Flaherty, Body Cavity Bombers: The New Martyrs—A Terrorism Research Center Book. Bloomington: iUniverse, 2013: 245.
[8] Using this analogy, CBRNE, with E dependent on use—as 9/11 utilized this form of weaponry (kinetic force and fuel loads of jet liners), can be viewed as dropping a rock into a pond rather than a pebble in that the disruptive surface ripples will be far larger.
[9] Components of this response, of course, include terrorist recruitment, funding, and other counter-organizational element focuses meant to deter, degrade, and ultimately eliminate terrorist groups operating locally and internationally via cooperation with partner nations.
Comments