© February 2015
This essay in the terrorism futures series will highlight the emergence of fifth dimensional battlespace, its implications for both the conduct of terrorism and counterterrorism operations, and, to some extent, interactions with terrorist disruptive targeting capabilities. Additionally, the larger civilizational context in which a dynamic yet little recognized terrorism and counterterrorism ‘fifth dimensional capabilities race’ that is taking place will be highlighted. While initially this concept may seem abstract, the importance of understanding its implications will become apparent.
Fifth Dimensional Battlespace
The concept of fifth dimensional battlespace is derived from the recognition of the growing influence of cyber (informational) and hyper (geometric) dimensionality on conflict and war. An early writer on the cyber component of this new form of space was William Gibson. He wrote the celebrated 1980s cyberpunk novel Neuromancer in which he defined cyberspace as:
A consensual hallucination experienced daily by billions of legitimate operators, in every nation, by children being taught mathematical concepts… A graphic representation of data abstracted from banks of every computer in the human system. Unthinkable complexity. Lines of light ranged in the nonspace of the mind, clusters and constellations of data. Like city lights, receding…[1]
Even earlier geometric artistic genres focusing on tesseracts and hypercubes—such as the Crucifixion (Corpus Hypercubus) by Salvador Dali in 1954—are also reflective of this emerging form of space-time interaction [2].
This form of advanced dimensionality—what was once only considered as relevant to 20th century art and science fiction—has in the 21st century been increasingly identified for its military and law enforcement applicability. The essential lesson learned is that human state forms and society build upon environmental and technological foundations as the energy basis of civilization (e.g. derived from human, animal, machine forms) has evolved over the course of many centuries. Along with this evolutionary process comes mastery of space-time dimensionality within increasing advanced forms of battlespace itself—whether it be the two dimensional battlespace of the ancients (x; line space + t; time) or the three dimensional battlespace of the medieval world (x,y; plane space + t; time). Thus, the battlespace—where humans fight and die—of antiquity or even the middle ages is fundamentally different in its level of sophistication (as are the armaments, armor, and even mounts utilized) compared to that which is presently utilized in our modern four dimensional world (See Fig. 1).
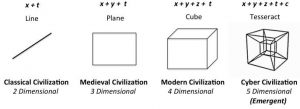
Source: Fifth Dimensional Operations: Space-Time-Cyber Dimensionality in Conflict and War—A Terrorism Research Center Book: 184.
Four dimensional battlespace, which is essentially composed of a maneuver and targeting box that is iterated in nature (x,y,z; cube space + t; time), has for roughly five-hundred years been the dominant physical area in which military forces have engaged one another. This form of battlespace, which the U.S. and coalition forces proved to have complete mastery of in the two Iraq Wars against Saddam Hussein (identifying and precision targeting his opposing military forces at will), however, is now beginning to near the end of its functional utility due to the advent of a more advanced form of battlespace derived from fifth dimensional attributes.
This form of emergent battlespace, which contains cyber (c) and hyper (h) elements of dimensionality, allows for the application of new informational and geometric based capabilities in conflict and war. One component of this advanced form of battlespace is the existence of a “human sensing dimensional barrier” that separates cyberspace (the fifth dimension) from humanspace (four dimensional space) even though they simultaneously exist together within the same physical area [3]. Another component of this form of battlespace is that of a force now able to engage in military activities that could not be conducted before due to restrictions imposed by earlier space-time barriers. With these barriers now overcome, qualitatively new warfighting capabilities are gained. As more and more components of fifth dimensional battlespace emerge, both terrorists and responding security forces will utilize them just as the military forces of more technologically advanced states are beginning to do [4].
Terrorism Implications
A five dimensional space analysis of defensive and offensive terrorist TTPs (tactics, techniques, and procedures) yields new insights into how these violent non-state actors engage in their operations. Terrorist use the defensive benefits of ‘cyberspace’ via stealth masking to dimensionally shift out of the killing ground of humanspace (e.g. four dimensional space). If it were not for this stealth masking capability, such forces would be easily acquired by security forces and either arrested or killed once inside sovereign state territories. Terrorist gain this dimensional shifting capability by means of a simple cost-effective cheat—they do not wear national military uniforms that identify them as enemy combatants. For advanced nation state forces—that follow the rules of warfare—to obtain a similar capability, they must field advanced (and costly) sensor defeating forces such as stealth aircraft that eliminate radar cross section (RCS), thermal emissions, and other signatures of their existence in physical space. In both instances—be it a terrorist or advanced stealth platform, they can be viewed as an invisible force that has defensively shifted (via spatial expansion—moving two points in space and time away from other) out of the killing zone of modern battlespace.
The offensive benefits of cyberspace provide terrorists with the ability to reach beyond the battlefield in which a tactical action takes place and influence civilian populations that are far away from the incident for psychological warfare (terroristic) purposes. The United States first truly encountered this phenomenon during the Vietnam War (a television war) and was finally defeated in that conflict due to the 1968 Tet Offensive which, while a physical victory for the U.S., lost that nation the war due to the final severing of its domestic bonds and relationships derived from disruptive targeting effects [5]. The term for the fifth dimensional capability that allowed the terrorizing of U.S. civilian populations which ultimately influenced the outcome of that war is known as spatial contraction [6]—the ability to take two points in time and space and bring them together (e.g. in this instance, civilians via media links to the battlefield). Over the course of decades, taped media shown during the evening news hour (which was delayed in its viewing) has been replaced with 24 hour news channels (that are more timely in their event broadcasting) and, ultimately, real time feeds and links by means of webcams, Skype, Tweets, and other social media technologies that have greatly increased offensive terrorist disruptive capabilities via this process of spatial contraction.
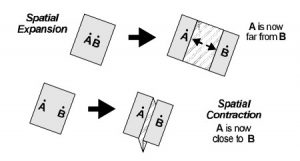
Source: Five-Dimensional (Cyber) Warfighting: 9.
Counter-Terrorism Implications
While the emergence of fifth dimensional space has provided both defensive and offensive capabilities to terrorists, it also has provided new capabilities to state security forces. As a result, a little noticed ‘fifth dimensional capabilities race’ has been taking place between terrorists and insurgents that wish to attack sovereign states and the public agents (police, security, and military personnel) that seek to defend them. One readily identifiable capability that is increasingly being utilized by state forces is the use of data fusion systems which attempt to identify stealth masked terrorists and bring them out of the defensive bastion of cyberspace into the killing (or capturing) ground of humanspace.
This is accomplished by piercing the “human sensing dimensional barrier” that stealth masked forces utilize thus allowing for them to then be acquired in time and space. Facial recognition and (less mature) ‘hostile intent’ technologies represent two examples of this process. They can be deployed at entry chokepoints, such as international airports, and are used to scan for terrorists attempting to enter national borders [7]. New body scanning machines—based on millimeter wave technology—in airports also fall into this countermeasure capability by looking for weapons hidden under clothing as do radar systems used by SWAT (special weapons and tactics) teams that can see movement and other activity (through physical walls) taking place inside terrorist hostage barricade situations.
New advanced weaponry capabilities—based on directed energy systems—that overcome prior space-time limitations (such as ballistics) are also emerging that state security forces can utilize against terrorist forces. These systems, such as the Active Denial System (ADS), allow for the generation of pain-inducing ‘energy barriers’ in physical space as well as the potential ability to counter terrorist human shield scenarios by incapacitating individuals (both the terrorist and the hostages/confederates) rather than utilizing deadly force [8]. The creation of ‘optical walls’ (laser based) to visually inhibit would-be suicide bombers from approaching security check points and ‘energy shields’ projected over facilities that pre-detonate mortar rounds fired by terrorist operatives readily provide additional examples of such capabilities [9].
Broader Context of Evolving Dimensionality and Change
Ultimately, the emergence of fifth dimensional battlespace as the new high ground (dimensionally speaking) in war and conflict, is representative of a shift from the modern (Westphalian state system) to the post-modern (successor and challenger state forms) era in human civilization. This shift is already underway in advanced economies with the fielding of 3D (three dimensional), and even newer 4D (four dimensional; self-assembly over time) [10], printing systems that are now beginning to both revolutionize post-industrial production processes as well as influence military logistics [11]. It is imperative within the context of these and other great scientific changes now taking place in our world—such as in the fields of bio- and nano-technology—that sovereign state forces learn how to achieve mastery of the capabilities offered by the post-modern battlespace. This must be accomplished, while at the same time, denying such mastery to terrorist forces that are readily seeking to do harm to sovereign states and their peoples.
Notes
[1] William Gibson, Neuromancer. New York: Ace Books, 1984: 51. This early definition of cyberspace has been linked to concepts of virtual reality, however, fifth dimensional space is far more encompassing than just an interactive artificial environment utilized by human beings.
[2] For an image of this work, see “The Collection Online: Crucifixion (Corpus Hypercubus).” The Metropolitan Museum of Art, http://www.metmuseum.org/collection/the-collection-online/search/488880.
[3] The military basis of this conceptualization of dual-dimensional battlespace was developed in Robert J. Bunker, “Advanced Battlespace and Cybermaneuver Concepts: Implications for Force XXI.” Parameters. Autumn 1996: 108-120, http://strategicstudiesinstitute.army.mil/pubs/parameters/Articles/96autumn/bunker.htm.
[4] For an overview and newer works on this advanced form of battlespace, see Robert J. Bunker and Charles “Sid” Heal, Editors, Fifth Dimensional Operations: Space-Time-Cyber Dimensionality in Conflict and War—A Terrorism Research Center Book. Bloomington: iUniverse, 2014.
[5] Hence, terrorist disruptive targeting and fifth dimensional capabilities are intimately linked together, see Robert J. Bunker, “Terrorism as Disruptive Targeting.” TRENDS Research & Advisory. January 2015, http://trendsinstitution.org/?p=870.
[6] On the flip side, the stealth masking (or dimensionally shifting) of forces can be viewed as spatial expansion. Two points in time and space that may be a few feet from one another, such as a terrorist standing in front of a state security officer, can for all intents and purposes be considered thousands of miles apart because the security officer cannot identify the terrorist as a threat but rather sees them as a random civilian (non-combatant).
[7] This, of course, means that state security forces know what the face of the terrorist entering into the nation looks like.
[8] For a primer on the ADS see U.S. Department of Defense, “Active Denial System FAQs.” Joint Non-Lethal Weapons Program, nd, http://jnlwp.defense.gov/About/FrequentlyAskedQuestions/ActiveDenialSystemFAQs.aspx.
[9] The ‘optical wall’ capability is attributed to the Laser Dazzler while the ‘energy dome’ capability is attributed to the Shortstop system.
[10] For more on 4D printing, see Skylar Tibbits, “The emergence of ‘4D printing.’” TED Talks. February 2013, http://www.ted.com/talks/skylar_tibbits_the_emergence_of_4d_printing?language=en.
[11] For military logistics concerning 3D spare parts fabrication, see Sydney J. Freeberg, Jr., “Navy Warship is Taking Printing to Sea; Don’t Expect a Revolution.” Breaking Defense. 22 April 2014, http://breakingdefense.com/2014/04/navy-carrier-is-taking-3d-printer-to-sea-dont-expect-a-revolution/, Adam Asclipiadis, “Rapid Equipping Force uses 3-D printing on the frontline.” U.S. Army. 9 July 2014, http://www.army.mil/article/129635/Rapid_Equipping_Force_uses_3_D_printing_on_the_frontline/, and Sarah Anderson, “China’s PLA Navy Deploys 3D Printers Onboard Warships to Replace Small Parts.” 3D Print. 8 January 2015, http://3dprint.com/35981/china-pla-navy-3d-printing/.
Comments